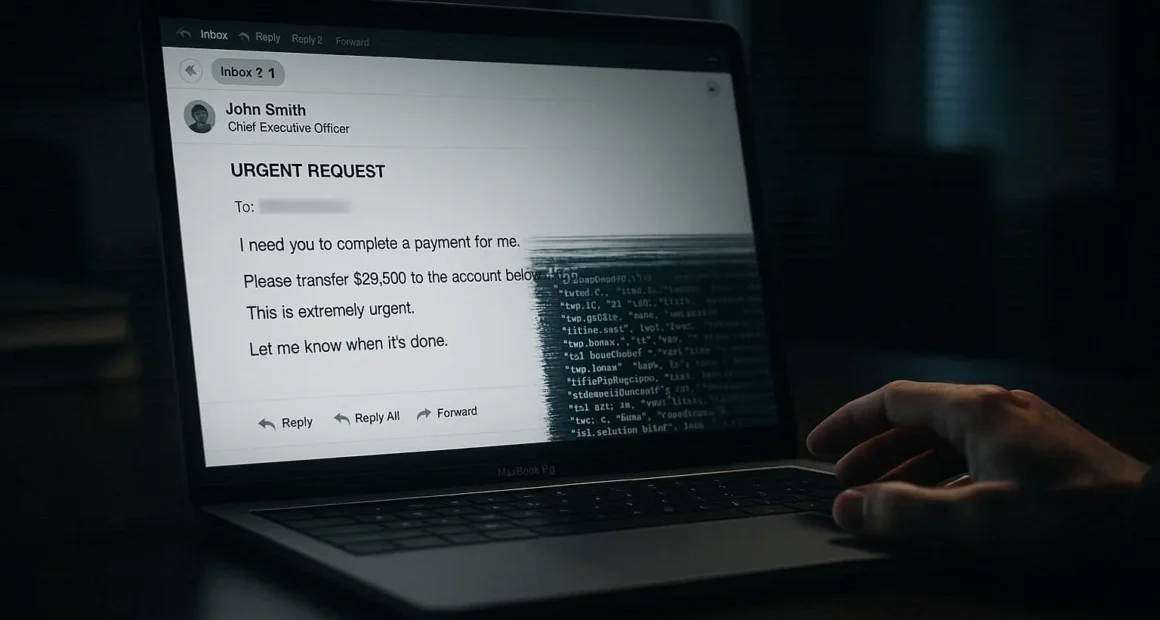
Rebecca Walsh opened the email from her CEO at 4:47 PM on a Friday. “Need you to process this wire transfer before close of business. Client emergency. Details attached.”
The writing style matched perfectly. The signature looked identical. The urgency felt typical. Rebecca processed the $847,000 wire transfer immediately.
The CEO never sent that email. The email phishing evolution had reached a terrifying new stage. Artificial intelligence had studied months of her boss’s correspondence and created a perfect forgery. Rebecca’s company lost everything.
The AI Weapons
Email phishing evolution in 2024 centers on artificial intelligence. Criminals feed AI systems thousands of emails from target companies. The AI learns writing patterns, corporate language, and communication styles.
Then it creates perfect forgeries in seconds.
The messages don’t contain spelling errors anymore. They don’t use awkward phrasing. They don’t trigger your instincts for danger. They read exactly like emails from real colleagues because AI has mastered human communication.
Moreover, the technology costs almost nothing. Criminals access AI tools for $20 monthly. That investment generates millions in stolen funds. The math is brutally efficient.
The Federal Bureau of Investigation reports that AI-powered phishing attacks increased 487% in 2024. The success rate jumped from 3% to 14%. Criminals steal $10.2 billion annually using these evolved tactics.
The predators have become exponentially more dangerous.

The Deepfake Voice Calls
Traditional phishing emails are just the beginning. Now, criminals follow emails with phone calls. But the voice on the phone isn’t human. It’s AI-generated audio that sounds exactly like your boss.
The email phishing evolution includes voice deepfakes. Criminals scrape audio from company videos, podcasts, or conference calls. AI analyzes the voice patterns. Then it generates realistic speech, saying whatever the criminals want.
Michael Chang, 41, received an urgent email from his CFO requesting a wire transfer. He called the number in the signature to verify. The CFO’s voice confirmed everything. Michael sent $623,400.
The real CFO was in a meeting with her phone silenced. The voice Michael heard was AI-generated. Perfect intonation. Correct speech patterns. Natural breathing sounds. Everything felt real.
Furthermore, the criminals knew Michael would call to verify. They anticipated his security training. They prepared the voice deepfake specifically for that verification call. Every defense he used was part of their plan.
The FBI warns that voice deepfakes appear in 41% of business email compromise attacks now. The technology has become standard criminal equipment. Your ears can’t be trusted anymore.
The Calendar Invasion
New email phishing evolution tactics exploit calendar systems. Criminals send meeting invitations that appear to come from legitimate colleagues. You accept the invitation. The meeting includes a link for “conference dial-in details.”
That link installs malware or leads to credential harvesting sites.
The calendar invitations bypass email security filters. They arrive directly through calendar applications. They look completely legitimate because they use real names from your organization’s directory.
Additionally, criminals now hijack actual email threads. They break into one person’s account. They read ongoing conversations. Then they insert themselves into active email chains with perfectly contextual messages.
Sarah Martinez received an email continuing a discussion with her vendor. The writing style matched. The details referenced their previous conversation. The link said “updated contract for review.”
Sarah clicked it. Criminals stole her login credentials. Within two hours, they’d accessed her company’s financial systems and transferred $1,347,000 to offshore accounts.
The email phishing evolution means attacks blend seamlessly into legitimate communication. There’s no obvious break in the conversation. No suspicious transition. The poison hides inside the normal business flow.
The LinkedIn Research Phase
Modern phishing attacks start weeks before you receive any email. Criminals study your LinkedIn profile. They identify your position, responsibilities, and connections. They learn your company’s structure and relationships.
Then they use that intelligence to craft targeted attacks. The Federal Trade Commission found that 76% of successful phishing attacks in 2024 involved prior social media research.
The criminals know your boss’s name. Your vendor relationships. Your work schedule. Your responsibilities. They use this information to create perfectly timed and contextually accurate phishing messages.
For instance, they notice you post about project deadlines. They send fake emails from vendors right when those deadlines approach. The timing creates natural urgency. Your stress makes you vulnerable.
Moreover, they identify out-of-office periods. When your boss travels, they impersonate them via email. When your IT staff attends conferences, they send fake tech support requests. The attacks target your moments of maximum vulnerability.
The QR Code Trap
The latest email phishing evolution weaponizes QR codes. Emails claim you need to verify your account or update security settings. Instead of clicking a link, you scan a QR code with your phone.
This bypasses computer security systems. Your phone’s security is usually weaker. The QR code redirects to fake login pages that steal credentials.
Furthermore, QR codes are harder to verify visually. You can’t hover over them to check the destination URL. You can’t examine the link structure. You just scan and hope.
The Cybersecurity and Infrastructure Security Agency reports that QR code phishing increased 312% in 2024[4]. The attacks target mobile devices specifically because phones have fewer security protections.
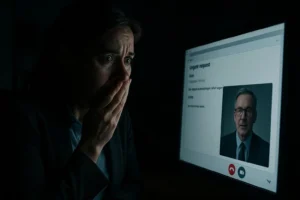
The Emotional Manipulation
James Rodriguez, 55, managed payroll for a construction company. He received an email from someone claiming to be a distressed employee. “My child is in the hospital. I need my paycheck deposited to a different account today. Please help.”
The email included hospital details. A photo of a sick child. Medical bills. Everything felt authentic and urgent.
James changed the direct deposit information. The next payroll cycle sent $12,400 to criminals. The employee’s actual paycheck never arrived. The child in the photo was stolen from social media.
The email phishing evolution now weaponizes human empathy. Criminals create elaborate emotional scenarios. They exploit your desire to help. Your compassion becomes their entry point.
Additionally, they use fear tactics. Fake emails from “IT Security” claim your account was compromised. “Legal Department” messages threaten consequences for policy violations. “HR” emails demand immediate response about disciplinary issues.
The emotional manipulation triggers panic. Panic shuts down critical thinking. That’s exactly what predators want.
The Supply Chain Infiltration
Criminals now compromise vendor email systems. They send invoices and payment requests from actual vendor accounts. The emails pass all authentication checks because they come from legitimate systems.
The only change is the bank account number. Everything else matches perfectly. Previous invoice formats. Correct contact information. Accurate project references.
The Department of Justice documented 2,847 cases of supply chain email phishing in 2024[5]. Companies lost an average of $438,000 per incident. The attacks are nearly impossible to detect because the email source is genuinely legitimate.
Moreover, criminals time these attacks perfectly. They monitor email conversations. When a real invoice is due, they intercept the communication and insert fake payment instructions. The timing makes verification seem unnecessary.

The Multifactor Authentication Bypass
You probably think multifactor authentication protects you. It doesn’t anymore. The email phishing evolution includes real-time credential harvesting.
Here’s how it works. You receive a fake login page. You enter your password. The system prompts for your authentication code. You provide it. Behind the scenes, criminals instantly use those credentials on the real site within the brief window before the code expires.
They’re in your account before you realize anything is wrong. Furthermore, they immediately change recovery options. They add new devices to your trusted list. They disable security notifications.
By the time you suspect a problem, they’ve already stolen everything they came for.
The Business Impact
These evolved attacks destroy companies. The Ponemon Institute found that 67% of businesses hit by advanced phishing lost over $500,000. 23% lost more than $2 million. 8% went bankrupt as a direct result.
Recovery is nearly impossible. Banks rarely refund wire transfers. Insurance claims face scrutiny and denials. Legal liability falls on the employees who processed fraudulent requests.
Additionally, the reputational damage spreads. Clients lose trust. Partners demand additional security. Regulators launch investigations. The attack continues, destroying value long after the money disappears.

Recognizing 2024’s Evolved Threats
Watch for these email phishing evolution warning signs:
- Urgent requests for wire transfers or credential changes
- Emails that continue existing conversations but introduce new links
- Calendar invitations with external links from internal contacts
- QR codes in security or verification emails
- Emotional appeals combined with time pressure
- Invoice payment instructions that differ from previous patterns
- Requests to use personal devices or bypass normal procedures
- Authentication requests for accounts you weren’t actively using
However, the most dangerous attacks won’t trigger any of these warnings. They’ll feel completely normal. That’s the terrifying truth about evolved phishing.
Protecting Against Evolution
Verify every financial request through a separate communication channel. If you receive an email about a wire transfer, call the person using a number from your previous records. Don’t use contact information from the suspicious email.
Furthermore, establish verbal verification codes. Choose secret words with colleagues for confirming urgent requests. The codes should never appear in any digital communication.
Also, implement mandatory delays for large transactions. No wire transfer over $50,000 should process same day. The waiting period allows time for verification and reflection.
Additionally, assume AI is creating the emails you receive. Question everything that requests action. Verify sources independently. Trust nothing that creates urgency.
Never click links in emails, even from known contacts. Navigate to websites manually. Never scan QR codes in security emails. Never provide authentication codes in response to unexpected prompts.
The Unstoppable Trend
The email phishing evolution will continue accelerating. AI will become more sophisticated. Deepfakes will become indistinguishable from reality. The attacks will blend deeper into legitimate communication.
Criminals invest millions in research and development. They test tactics on millions of targets. They refine approaches based on success data. They evolve faster than defenses can adapt.
Meanwhile, you’re trying to work. You’re managing deadlines. You’re juggling responsibilities. You can’t scrutinize every email with forensic intensity. The predators know this. They’re counting on it.
The email in your inbox right now might be AI-generated. The voice on your next conference call might be deepfake audio. The urgent request from your boss might be criminals who studied your company for weeks.
You’ll never know until it’s too late. That’s the horror of evolved phishing. The attack looks identical to legitimate communication. Your instincts can’t protect you. Your training can’t save you. Your technology can’t stop it.
Trust nothing. Verify everything. Survive desperately. The predators have evolved beyond your ability to recognize them. And they’re already reading your email.
Resources
[2] Federal Bureau of Investigation. “Business Email Compromise.
[3] CISA. “Avoiding Social Engineering and Phishing Attacks.”
[4] Federal Trade Commission. “Scammers hide harmful links in QR codes to steal your information.”
Related reading(suggested)
Fake Antivirus Software: How Scareware Bleeds You Dry
Tech Support Scams: Microsoft/Apple Impersonators Exposed